AXIOM Remote/Development
1 Introduction
Currently Axiom Remote Development kit has 3 main components,
- AXIOM Remote
- FT4232H mini- module
- Pickit
2 Pickit Connection
2.1 Steps to connect and flash AXIOM Remote with Pickit2
- Connect the 6 pin cable between pickit and ICSP port on Remote.
Note : Make sure that the pin 1 (indicated by white arrow) of the wire is connected to pin 1 (indicated by white arrow) on the ICSP port on the remote. - Use pic32prog to flash the hex file to AXIOM remote.
Note : pic32prog only works with sudo - Press the reset button on Remote After the flash progress is complete in pic32prog.
3 UART Connection
Any UART to USB adapter should work. We use an FT4232H adapter that is available from distributors for around 28€. You require a USB-A to USB-Mini-B cable to connect the FT4232H to your computer and 3 dupont cables to connect the FT4232H to the AXIOM Remote.
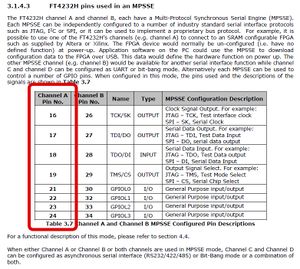
3.1 FT4232H Pinout
Chip Datasheet: https://ftdichip.com/wp-content/uploads/2020/08/DS_FT4232H.pdf
Mini Module Datasheet: https://www.ftdichip.com/Support/Documents/DataSheets/Modules/DS_FT4232H_Mini_Module.pdf
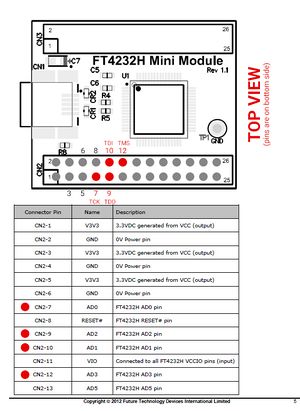
3.2 FT4232H wiring
FT4232H features 4 UART ports, in this example we utilize port C. Under Linux the FT4232H should simply show up as ports /dev/ttyUSB0 to /dev/ttyUSB3 where port C from the above example would correspond to /dev/ttyUSB2.
Note that the Transmit (TXD) and Receive (RCD) lines need to be cross wired meaning TXD needs to be connected to RXD and RXD to TXD. You can choose any GND pin though.
| Name | FT4232H pin | Remote pin |
|---|---|---|
| GND | GND | GND |
| TXD | CD0 | RXD |
| RXD | CD1 | TXD |
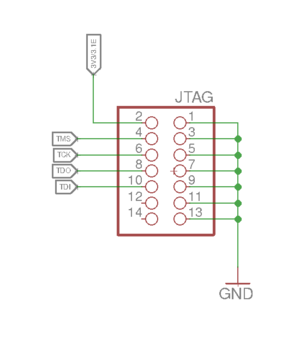
4 JTAG connection
4.1 FT4232H wiring
5 dupont cables are required to hook up JTAG to the FT4232H.
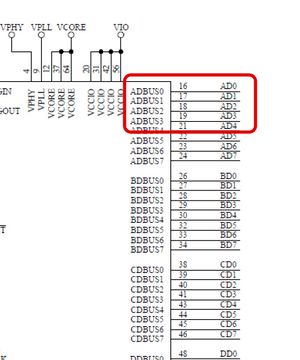
| Name | FT4232H pin | Remote pin |
|---|---|---|
| GND | GND | GND |
| TCK | AD0 | TCK |
| TDI | AD1 | TDI |
| TDO | AD2 | TDO |
| TMS | AD3 | TMS |
4.2 Flashing
It is possible to flash the PIC32 firmware through pic32prog and FT2232H and FT4232H adapters (amongst others, like PICkit3). Multiple devices which use FT2232H are already supported in pic32prog, but not FT4232H. We've forked pic32prog, added FT4232H support and adjusted the build to reduce problems there.
https://github.com/apertus-open-source-cinema/pic32prog
Usage example:
./pic32prog -s 1500 -S AXIOM_Remote_Firmware_635.hex
Output:
Programmer for Microchip PIC32 microcontrollers, Version 2.0.258
Copyright: (C) 2011-2015 Serge Vakulenko
IDCODE=5510e053
Adapter: Generic FT4232H adapter
Processor: MZ2048ECG100
Flash memory: 2048 kbytes
Boot memory: 80 kbytes
Data: 135904 bytes
Erase: .......done
Program flash: ################################## done
Program boot: ### done
Program rate: 35484 bytes per second
Note: Don't forget to press reset button after flashing, as by default reset (MCLR) will be hold by the programmer.
4.3 Debugging
Our tests with OpenOCD and FT4232H were only partially successful, PIC32 could be accessed, resetted and halted, also registers and disassembled code inspected, but breakpoints could not be set properly or were not stopping the execution. Luckily there is a tool called ejtagproxy, which can be used instead of OpenOCD. Also the connection from gdb-multiarch is working properly and breakpoints are stopping the execution.
ejtagproxy supports same devices as pic32prog. We've forked ejtagproxy' too and added FT4232H support.
https://github.com/apertus-open-source-cinema/ejtagproxy
Note: Use gdb-multiarch which is able to debug MIPS targets.
Start ejtagproxy:
./ejtagproxy
Output:
GDB proxy for Microchip PIC32 processors, Version 1.0.36 Copyright (C) 2012 Serge Vakulenko EJTAGproxy comes with ABSOLUTELY NO WARRANTY; for details use '--warranty' option. This is Open Source software. You are welcome to redistribute it under certain conditions. Use the '--copying' option for details. ejtagproxy: waiting on TCP port 2000
Start gdb-multiarch':
gdb-multiarch
Connect to ejtagproxy:
target extended-remote localhost:2000
or
tar ext :2000
Load symbol file (to see the names of function where the target was halted, instead of addresses, and to be able to set breakpoints via names and not only addresses):
file <path to .elf file>
Example
file /home/dev/Projects/Firmware/build/AXIOM_Remote_Firmware_635.elf
Some useful commands:
| Command | Short form | Description |
|---|---|---|
| reset | r | Reset target (PIC32) |
| CTRL+C | Halt the target | |
| continue | c | Resume execution after halt |
| break PollButtons | b PollButtons | Set breakpoint on function PollButtons |
| break 0x9d001f73 | b 0x9d001f73 | Set breakpoint on address 0x9d001f73 |
| info breakpoints | i b | Show set breakpoints |
| delete | del or d | Delete all breakpoints |
| delete breakpoint 3 | del 3 or d 3 | Delete breakpoint 3, see 'info breakpoints' |
| info registers | i r | Show available registers and their values |
4.3.1 Debugging in VSCode
TODO